 |  |  |  |  |  |  | | November 10, 2011
THIRTYSEVEN4 MOBILE SECURITY IN THE NEWS
We take educating users on the latest cyber dangers very seriously, and have been blessed to recently partner with both local (ie. FOX 8, Akron Beacon Journal, etc.) and national media outlets in spreading the word about emerging threats. |
| |
 |  | | If you didn’t get a chance to see last nights airing on Fox 8 Cleveland, you can view the whole segment at:
http://www.fox8.com/health/parenting/ and by clicking on the “Cell Phone Viruses” video.
In an effort to increase awareness of the risks associated with mobile devices (smartphones, tablets), we have created and posted the following webpage outlining some tips and procedures to protect yourself and your mobile device.
Tips to protect yourself and your phone
Additionally, if you’re involved in corporate training of employee’s or in education and want to educate your staff (or students) on the dangers of Smartphones, we have already released a poster series dedicated to Mobile Security and developed other literature. If interested, please email partnership@thirtyseven4.com.
posted by Steven Sundermeier |
|
|  |  |  |  |  |  |  |  | | October 7, 2011
QR CODES EXPLOITED
As it was reported earlier this week, malware authors have found an easy way to get their malicious creations installed on Android devices...the new technique utilizes QR codes.
QR (Quick Response) codes are a form of a matrix barcode,that contain and encoded form of data (for example: to store the URL/website information). Scanning QR Codes are a convenient way for a user to open a website directly, opposed to typing in the whole website address.
In the case below a malware author has used a malicious QR Code to redirect unknowing users to malicious websites that install a new Trojan. Essentially, when a user scans the QR Code with their Android device, the code redirects them to a site that will install a Trojan (now found in-the-wild) on to their phone. Once installed, the Trojan will attempt to deliver a number of SMS messages to premium-rate numbers.
The installed icon of the Application looks like:
And during installation, it asks the user for the following permissions below:
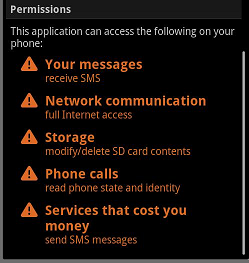
Here is how the Trojan send messages to the premium rate numbers.
Thirtyseven4 Mobile Security detects the file as TrojanSMS.AndroidOS.Jifake.f. An extended trial license of Thirtyseven4 Mobile Security is available here.
posted by Steven Sundermeier | | | | September 29, 2011
ANDROID MALWARE INCREASING
As I was quoted saying in our press release yesterday (available here), the popularity of Android devices are lending itself to a rapid increase in malware created specifically for Android-based smartphones and tablets. These malware (some already out in-the-wild) pose a serious threat to Android Users and the confidential information often times stored on there phones and tablets. And while mobile malware is intercepted by our virus research team on a daily basis, I thought I'd describe a few recent examples:
Case 1: Android.RogueSPPush.A
Android.RogueSPPush.A is a relatively new malware that targets Android Users (specifically Chinese Android Users). It targets unknowing users by using a SMS-based subscription system to sign-up users for certain services without the user’s knowledge and consent. If successful, the Android users will end up suffering potentially significant financial losses.
Looking at a Chinese SMS based subscription, the process involves three stages.
1.) A user sends a service-subscribing SMS message to a defined service provider.
2.) The service provider replies back to the user a service confirming SMS message containing the detailed information of the service
3.) The user will have to confirm the subscription by replying back to the SMS message with the recommended "Y."
After installation, the installed icon will look as follows.

As described above, the malware will send the confirmation with the text ‘Y’ to complete the process.
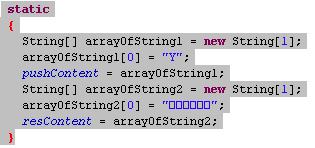
The malware will then send the SMS with the confirmation to the service provider.
Thirtyseven4 Mobile Security (TS4Android) detects this malware as Android.RogueSPPush.A
Case 2: Android.Lotoor.B - an Android malware now establishing Root privileges
Android.Lotoor.B is a newer type of malware attacking the latest version of the Android operating system, version 2.3 (Gingerbread). This new malware has already been seen "in-the-wild" and masquerading as an app featuring the "Beauty of the Day" pictures.
Package1 downloaded uses the following permissions:
android.permission.READ_PHONE_STATE
android.permission.READ_LOGS
android.permission.DELETE_CACHE_FILES
android.permission.ACCESS_CACHE_FILESYSTEM
android.permission.WRITE_SECURE_SETTINGS
android.permission.ACCESS_NETWORK_STATE
android.permission.INTERNET
android.permission.WRITE_EXTERNAL_STORAGE
android.permission.MOUNT_UNMOUNT_FILESYSTEMS
android.permission.READ_OWNER_DATA
android.permission.WRITE_OWNER_DATA
android.permission.WRITE_SETTINGS
com.android.launcher.permission.INSTALL_SHORTCUT
com.android.launcher.permission.UNINSTALL_SHORTCUT
android.permission.RECEIVE_BOOT_COMPLETED
android.permission.RESTART_PACKAGES
Using Gingerbreak, and utilizing the latest exploit for gaining root access to Gingerbread, the malware gathers information about the infected device and sends it to remote servers. In addition to gathering and reporting the IMEI, phone number and SIM serial number, GingerMaster creates a backdoor root shell, stored in the system partition in an attempt to survive after software upgrades, to allow for an attacker to access the device.
Thirtyseven4 Mobile Security for Android (TS4Android) detects these files as Android.Lotoor.B.
posted by Steven Sundermeier | | | | September 2, 2011
Information on Worm Morto
There has been a lot of news coverage, based on a warning issued by Microsoft, regarding a new Internet Worm dubbed "Morto". Morto is a worm that spreads to systems through the use of the Remote Desktop Protocol (RDP) Port. Essentially, it attempts to connect to a remote machine by scanning the RDP Port on the network, this scanning causes a lot of network traffic for port 3389/TCP (the RDP Port). We have posted a complete description for Morto here.
The most important thing is that our Virus Research Team immediately updated for this new threat and Thirtyseven4 Users are fully protected against Worm.Morto. Protection was released on August 28th, 2011
Posted by Steven Sundermeier | | | | July 15, 2011
THIRTYSEVEN4 - “THANK YOU”
As the owner of Thirtyseven4, I wanted to say “thanks” to all our customers for making Thirtyseven4 their antivirus of choice- quarterly sales were at an all-time high. We have been very blessed by your support and humbled by all the positive e-mails we have been receiving.
Here’s one such example:
"Thanks for everything so far. I just wrote a very strong recommendation of your product to our region's tech director mailing list. If it were up to me, I'd have the whole state running your software! You guys have been rock stars from the get-go, from installation right up to now. Please share my thanks and attaboys with the rest of your staff, and keep up the awesome work!"
-Jimmy Fisher, Winters ISD
More importantly, through your support, we were able to financially fill the sponsorship gaps of over 180 young girls [this quarter alone] through our partnership with Remember Nhu, “Thank you.”

posted by Steven Sundermeier | | | | June 9, 2011
Thirtyseven4 Antivirus - Good Time to Upgrade
With the weather getting warmer and schools now letting out for the summer, it may be a great time to upgrade your older Thirtyseven4 installations to the latest version. Or better yet, a great time to transition off your existing antivirus provider to Thirtyseven4 Antivirus.
Thirtyseven4 Antivirus offers a 5-in-1 protection suite that includes, Antivirus, AntiMalware (detection and removal), AntiRootkit, Firewall and Data Theft Prevention.
posted by Steven Sundermeier | | | | June 2, 2011
Thirtyseven4 Admin Console 4.5 Service Pack 1 Released
This week we released Service Pack 1 (SP1) for users running Admin Console 4.5. In order to apply SP1, from your Admin Console system, navigate to C:\Program Files\Thirtyseven4\Thirtyseven4 Admin Console 4.5\Admin\web\builds and execute the file, “acsvpack.exe“.
posted by Steven Sundermeier | | |  |  | | May 31, 2011
Scareware Increasing - Thirtyseven4 Antivirus Creates Dedicated Tools
Over the past few weeks, here at Thirtyseven4, we have updated for a record number of Scareware type applications this month. I’m very happy to report great success against these threats largely due to our proactive, behavioral-based, DNA Scanner. Unfortunately, for a variety of reasons, it seems other users of competing products aren’t doing so well. As a company, we have decided to offer our help to users who may have (or may be) experiencing a Scareware type infection without having to purchase anything. Here’s what we suggest:
- Download the following Generic Rogueware Removal Tool (this tool will not only scan your system for specified Scareware but will also restore Internet connections in the event it was broken due to the infection). You can download here.
- Uninstall your existing antivirus software application (temporarily) and after a system reboot, install the Thirtyseven4 Antivirus evaluation copy (here).
You can also check out our webpage dedicated to bringing the latest information on Scareware.
posted by Steven Sundermeier |
 |  | | May 16, 2011
Thirtyseven4 Antivirus Testimonies
It has now been a couple of weeks since the launch of Admin Console 4.5 and version 12 of the Client and I'm proud to report that the new versions have been very well received.
For example:
"Love it!!!! Designed quite well and to me more user friendly. At least for IT ... everything locked down on client side...Got to Love IT!!!!"
- Technology Coordinator, Texas School District
"Great job on version 12 of the client, I do like the new interface a lot!"
- Technology Coordinator, New Jersey School District
One of the biggest questions we’ve received is how all the new features (advanced Browser Protection, silent Firewall, automated Rogueware scanner with full malware removal, etc.) affects the performance. To quote one of my favorite Disney characters, Lightning McQueen..."Speed. I am [we are] speed."...that is, not only have we introduced new, cutting edge technologies but we also took our lightweight, fast antivirus solution and made it faster.
Anyone looking for a lightweight, fast antivirus solution that offers full detection and removal of all forms of malware, I highly recommend checking out Thirtyseven4 Antivirus
posted by Steven Sundermeier |
 |  | | May 02, 2011
THIRTYSEVEN4 ANTIVIRUS VERSION 12 HAS ARRIVED
As the owner of Thirtyseven4, I’m very proud to announce the release of Thirtyseven4 Antivirus version 12.0 (the official press release can be seen here). A lot of time, energy and effort has gone into the making of this release. All our users who are familiar with our past and current releases will immediately notice a completely redesigned user interface. We feel the new Thirtyseven4 Antivirus interface makeover makes us the easiest antivirus product on the market to use. In addition to the cosmetic changes in v.12.0, Thirtyseven4 Antivirus now includes many new and exciting features such as:
Silent Firewall - Includes both an Intrusion Detection System & Intrusion Prevention System
Advanced Browser Protection - Hundreds of malicious websites (URL’s) are being added daily to proactively block scareware (fake security applications) and other forms of malware from being downloaded. Browser Protection supports all major web browsers
Automatic Silent AntiMalware Scans - We have taken our industry leading AntiMalware module and made it even better. AntiMalware can now be configured to perform automated, periodic malware scans
Improved Entertainment Mode System - A unique, Thirtyseven4 specific feature essential for schools
Additional Deployment Support - Already with multiple, easy methods for deploying the Client from the Admin Console, the Admin Console now supports additional ways.
Download or Purchase your copy of Thirtyseven4 Antivirus today and please stay tuned for other soon to be released product announcements.
As with any software upgrade or new release we strongly urge customers to test the new builds in their environment prior to installing network wide.
We have also posted upgrading instructions to the latest Admin Console 4.5 here and upgrading instructions of a previous stand-alone version of Thirtyseven4 Antivirus to version 12.0 here.
posted by Steven Sundermeier |
 |  | | April 12, 2011
Yahoo Messenger Worm Spreading
We have recently posted a virus description for Worm.Ckbface.adj. This particular worm is spreading via Yahoo Instant Messenger by masquerading as a photo from a friend. If a user is tricked by the false claim, they will unknowingly download and install a backdoor. If the file is executed, their system will become infected and all their contacts will be sent the malicious message. The affected systems will also be turned into a hotbed for advertising.
More more information can be seen the Worm.Ckbface.abj description.
Posted by Steven Sundermeier |
 |  | | March 1, 2011
As I wrote in a previous blog, I had the opportunity in January to sit down with the Fox 8 Team to discuss the dangers of posting photo’s online on popular social networking sites like Facebook, Myspace, etc.
I was honored to once again have the opportunity to share additional insights (this time) on the Fox 8 Morning Show. Please tune-in to the segment- it will deal with the risks associated with smart phones. One area of concern is with their advanced camera features and their built-in Geotags feature that is enabled by default.
posted by Steven Sundermeier |
| |
 |  | | January 18, 2011
New 2011 Security Posters Now Available
I’m proud to announce the release of our new poster series for 2011. In collaboration with school systems across the country, we decided to release two new posters this year since there were two major hot topics that they wanted help with in educating their staff and students: Scareware (ie. the fake security applications) and Hacking (legal ramifications). The complete press release can be see here.
For those who may be new with Thirtyseven4 and our services, the educational posters are free to any school system. Helping schools is at the heart of our business. We know the more we can to help schools stay protected against the latest threats the better and we fully understand educating students and staff is a best first step. If you are interested in the posters simply fill out the request form located here.
To learn more about how Thirtyseven4 Antivirus can protect your schools computer and how cost affordable pricing, please click here.
posted Steven Sundermeier |
| |
 |  | | January 5, 2011
As recognized local security experts, Thirtyseven4 had the privilege to host members of the Fox 8 Cleveland team yesterday. During their visit, I had the opportunity to interview with and share my thoughts with a Fox 8 reporter on the growing risks of sharing photo’s online and steps that parents can do to help secure their children’s digital footprints.
As a result of the interview, I felt it would be important to publish some of the information that was discussed with our customers as well (since the news report is limited to the local viewing area). I have created the following page to help educate parents on the dangers associated with posting files online (click here).
posted by Steven Sundermeier |
| |
 |  | | January 3, 2011
Thirtyseven4 Conferences Announced
I’d like to start my first blog of 2011 by wishing you all a blessed upcoming New Year! The entire Thirtyseven4 Team is looking forward to another successful year serving and protecting you. And as I mentioned on my last blog (of 2010), we have a lot of great announcements forthcoming in the new year.
One announcement I’d like to start the new year making is that starting this month we will begin taking our industry leading antivirus solution, Thirtyseven4 Antivirus on the road to some of the leading technology conferences. Please check out the following webpage (click here) to learn more about the conferences we’re planning on attending.
posted by Steven Sundermeier |
| |
|
|
|
|  | | “Delight yourself in the Lord and he will give you the desires of your heart.” Psalm 37:4 |
|