|  |
 |  |  |  |  |  |  |  |  |  |  |  |  |  |  |  |  |
| Click here for the current Blog | |
|
| July 29, 2010
Black Hat Conference in Las Vegas
As many of you know, the Black Hat 2010 convention took place in Las Vegas yesterday and today. I was unable to make it to the convention this year but have been doing my best to closely follow the latest news out of Las Vegas. As expected, there were many excellent presentations and speakers. One of the stories that caught my eye was the talk on hacking into stand-alone ATM machines both physically and remotely. It was my understanding that this presentation was prepared for last year but due to fears that “patches” wouldn’t be in place in time to prevent future attacks, the speech was postponed until this year. If interested, I've included a few decent reads on the topic below:
http://www.blackhat.com/html/bh-us-10/bh-us-10-briefings.html#Jack
http://finance.yahoo.com/news/Bunkerbusting-ATM-attacks-apf-439535708.html?x=0
posted by Steven Sundermeier | |
|
| July 23, 2010
STUXNET WORM/TROJAN/ROOTKIT - WHAT IS IT?
By now, I’m sure you heard or read a blog or two about the new piece of malware called StuxNet. You’re not alone. It seems StuxNet has created a heightened buzz within the media and security community. It has also lead to many varying opinions and beliefs on the origin and reasons for its creation.
Let me first begin by letting you know that Thirtyseven4 customers are completely protected against the StuxNet threat. Thirtyseven4 customers are even proactively protected against unknown threats like StuxNet that utilize a similar technique.
In case you haven’t read much about it, StuxNet is a sophisticated exploit of a simple design flaw within Windows Shell. If you didn’t catch that...StuxNet exploits a design flaw within the Windows Shell and not a vulnerability as many people are falsely blogging. How it works is that it disguises itself as a shortcut file (this is a file type that carries the .LNK file extension) utilizing USB-based Removable Drives as a medium to propagate itself on to targeted systems. The inherent flaw in the Microsoft Windows Shell permits the maliciously created shortcut file to be self-executed simply by viewing the contents of used Removable Drive in Windows Explorer.
User who aren’t protecting their systems with Thirtyseven4 Antivirus and who are infected (a sure sign would be seeing the automatic creation of .LNK files on your plugged in Removable Drives), I highly encourage you to download a copy of our trial software. We desire to assist you.
To address this critical issue, Microsoft has released the following emergency security bulletin with possible “workarounds” (http://www.microsoft.com/technet/security/advisory/2286198.mspx).
posted by Steven Sundermeier | |
|
| July 16, 2010
MICROSOFT’S JULY 2010 SECURITY BULLETIN RELEASED
Earlier this week, Microsoft released their July 2010 Security Bulletin- the Security Bulletin addresses five vulnerabilities with three of them deemed as “critical”. More information can be viewed from:
http://www.microsoft.com/technet/security/bulletin/ms10-jul.mspx
posted by Steven Sundermeier | |
|
| July 11, 2010 (* Updated July 13, 2010)
SCAREWARE NO LONGER A THREAT - THINK AGAIN
You may remember that towards the end of May of this year, it was widely reported by media outlets and security firms of the arrest of three scareware authors. These authors were said to have grossed more than $100 million during their operating days. Those of you who believed this public announcement would slow down the activity of other scareware criminals will need to think again...as our team has seen the exact opposite. Scareware and other forms of Rogueware continue to be on the increase. In the last few days, we’ve added detection AND removal routines for a whole new wave of these type of infections. Please know Thirtyseven4 takes these types of infections very serious and we have a dedicated team in multiple global locations scanning the Internet to protect our customers. A few of the recently added ones include: Defense Center and AntiSpyware Soft.
* I have updated this blog post to include another recently added piece of Rogueware called “AntiMalware Doctor”. Up-to-date Thirtyseven4 Antivirus users are 100% protected against this threat.
posted by Steven Sundermeier | |
|
| July 6, 2010
VIRUS DESCRIPTIONS
Our customer service department recently received a phone call asking if we had any further information concerning a fake antivirus application called “Antivirus Soft”. He had recently downloaded and installed a competing free antivirus solution and now found himself infected. Our team pointed him to a free trial license of Thirtyseven4 which was able to clean his PC. He mentioned how it would be nice to have a description of this malware. We quickly explained we already did, and to bookmark our Latest Virus description page. We a graphic linking to our Latest Virus description page on the front page of thirtyseven4.com (shown below). The direct link is: http://www.thirtyseven4.com/virus.html Please bookmark if you haven’t already done so.

posted Steven Sundermeier | |
|
| July 2, 2010
July 4th Weekend
On behalf of the Thirtyseven4 Team, I’d like to wish you all a nice and safe July 4th weekend. In observance of the July 4h holiday, the Thirtyseven4 offices will be closed on Monday, July 5th, 2010. Anyone needing immediate assistance can contact level2support@thirtyseven4.com and one of our after (normal business) hour support technicians will be immediately notified.
Please note that our virus research team will continue to work around the clock over the holiday weekend making sure you are protected against the latest threats.
posted by Steven Sundermeier | |
|
| June 28, 2010
LAST CHANCE: Free Educational Program Set To Expire On June 30th, 2010
Here at Thirtyseven4, it has always been our mission to help schools any way we can. This past April we launched a free educational program where we literally were giving away licenses for free in an effort to help under funded school systems. After a very successful initiative (we gave away well-over a hundred licenses to school systems across the United States and Canada), the campaign is drawing to close in a couple of days. There are a few days left, so if your school (or you know of a school who) could use the free licenses, please sign up today before the program expires.
Learn more:
http://www.thirtyseven4.com/school.html
I want personally thank all the school systems who took advantage of the offer and placed their trust in Thirtyseven4 Antivirus
posted by Steven Sundermeier | |
|
| June 22, 2010
COMMITMENT TO OUR CUSTOMERS
Usually, I blog about all the junk mail (spam, phishing scams, etc) I receive, however today I’d like to share a nice email I received yesterday. “Steven,
...I must tell you that you are receiving rave reviews for the product and customer service/support. They can't seem to say enough about what a great experience they have had with your company. Thought you might enjoy hearing that.”
Here at Thirtyseven4, courteous and dedicated customer service is our top priority and defines our business relationships.
posted by Steven Sundermeier | |
|
| June 11, 2010
June Microsoft Security Bulletin Released
Microsoft has released its security bulletin for June 2010. This month Microsoft has released 10 bulletins, addressing a total of 30 vulnerabilities. More information on the bulletin can be seen from:
http://www.microsoft.com/technet/security/bulletin/ms10-jun.mspx
posted by Steven Sundermeier | |
|
| June 9, 2010
Friendship Opportunities Abound
It seems my popularity as been soaring lately as men and woman from around the world are seeking “friendship” with me (see a sample email below). The amazing thing is that some one these junk messages are reaching me at relatively unpublished and unused email addresses. I will report back in a later blog of the “what would happen” if you actually responded by to these spam messages. My team and I will begin our investigation shortly. Stay tuned ...
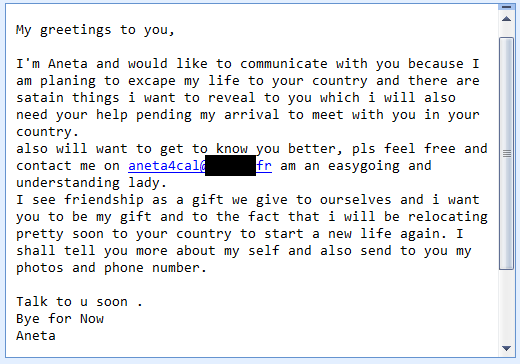
posted by Steven Sundermeier | |
|
| June 4, 2010
ADMIN CONSOLE 4.2 UPDATED
Customers across the United States have spoken and we have listened again. I proud to announce an update to our Thirtyseven4 Admin Console (AC) 4.2. All changes in this release are a direct result of feedback from our customers. So, in this intermediate release we have made our already ease to install AC that much easier.
Changes include:
1. Thirtyseven4 Messenger is turned OFF by default.
2. Client Packager can also be created with /silent parameter.
3. Installation is now possible on the remote system using Domain Administrator. To install the client on a system under a domain you’ll need to specify User Name in DOMAINNAME/USER NAME format. Where DOMAINNAME is the name of the domain and USER NAME is the name of the Domain Administrator.
We greatly value all the wonderful feedback we have been receiving. Any additional suggestions and/or questions can be directed to service@thirtyseven4.com.
posted by: Steven Sundermeier | |
|
| June 1, 2010
OHIO BUSINESS OWNERS BE ON ALERT
As an Ohio business owner, I recently received an alert notice from the Ohio Business Gateway (OBG). According to the alert the “OBG Electronic Filing has received reports of illegitimate phishing e-mails being sent to OBG users. The email is not from the State of Ohio and it should be deleted.”
The OBG is alerting its users that they do not need to install or update any software in order to continue using the Ohio Business Gateway after June 1, as per the false claim. The alert also makes it clear that distributing “software via links in email is not, and has never been, a standard business practice of the Ohio Business Gateway.” This is phishing scam is very well done, so Thirtyseven4 is alerting all Ohio business owners to delete the phishing email if received.
An example email is shown below:
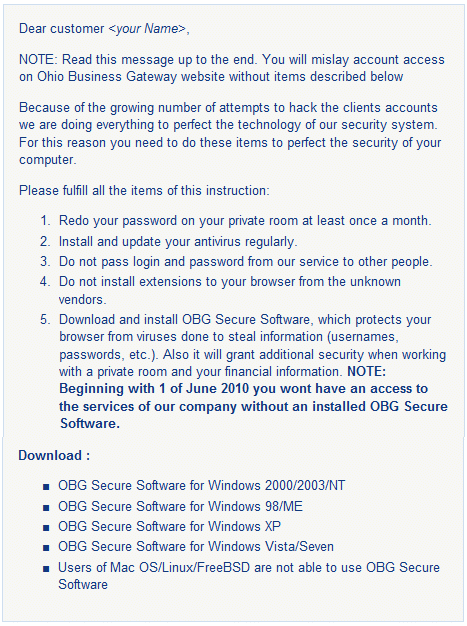
Further information can be read from the Ohio Business Gateway website at: http://business.ohio.gov/alert/
posted by Steven Sundermeier | |
|
| Archived Blogs
August 1, 2010 - September 30, 2010
June 1, 2010 - July 31, 2010
April 1, 2010 - May 31, 2010
January 2010 - March 2010 | |
|
| | |