 |  |  |  | |  | |  | | |  |  |  |  |  |  |  |  |  |  |  |  |  |  | | Click here for the current Blog | | | | March 29, 2010:
POLYMORPHIC FRAUDTOOL
Another day, another piece of rogueware. Late last week we intercepted a new polymorphic fraudtool, Fraudtool.AntivirusSoft (a screen is shown below) and a complete description of this Fraud Tool can be seen here. This particular one is extremely nasty and very hard to remove if it gets mistakenly / unknowingly installed. I can’t stress how important it is to not click “Yes”, “Ok”, “I Agree”, etc when prompted by such applications to do so.
Fraudtool.AntivirusSoft appears as follows:
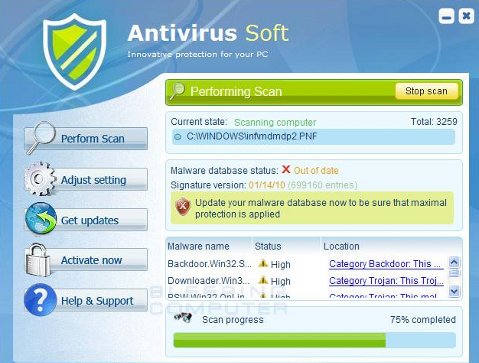
Thirtyseven4 Antivirus has been updated for such a threat along with the required removal routines.
posted by Steven Sundermeier | | | | March 23, 2010
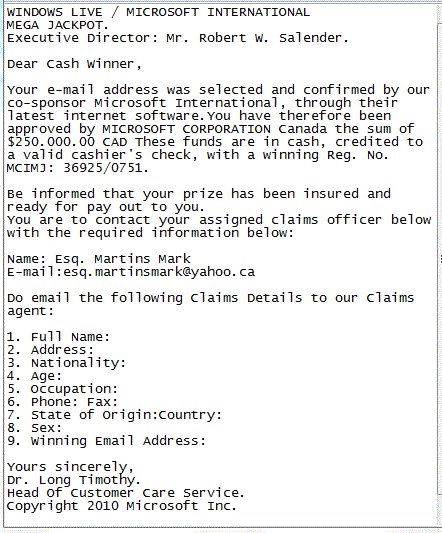
DRAW NOTIFICATION - MEGA JACKPOT
If you have been as lucky (or unlucky) as me, you probably have received a couple similar messages (below) in the last few weeks claiming you have won a mega jackpot. Prize amounts may vary, as well as, the co- sponsor (in this case Microsoft) but the objective of trying to retrieve your information for malicious purposes does not. It’s funny how everyone is a such a big winner when no one ever signed up for anything. I also find it humorous when these so -called “Microsoft” employee’s are sending out corporate emails from gmail accounts. If you should receive an email like this- delete it right away. It is a scam.
posted by Steven Sundermeier | | | | March 18, 2010
SAFE WEB SEARCHES - MORE INFORMATION
We recently did a press release on the dangers of performing online searches and since all the information we wanted to include couldn't fit within the formatting guidelines, I thought I'd fill in some of the missing information. In the release we posted five simple steps to lessen the chance of falling victim to SEO poisoning- here are the five steps again with a little more elaboration and helpful links.
1. When searching hot news topics, go to a reputable news source website by typing in the web address directly in to the browser. Along these same lines, you can add a few news web sites of your liking to your Favorites for easy future access.
2. When visiting less trusted websites for the first time, enable the secure browsing feature of the browser. A couple examples would be "InPrivate Browsing" within Internet Explorer or "Private Browsing" within Firefox. You follow the links below for a detailed explanation on how to turn on the settings.
Internet Explorer - InPrivate Browsing
http://www.microsoft.com/windows/internet-explorer/features/safer.aspx
Firefox - Private Browsing
http://support.mozilla.com/en-US/kb/private+browsing
3. Never click ‘Ok’, ’Yes’, or similar if a message box should appear seeking or giving permission to install some component, object or feature, when visiting unknown websites
4. Make sure that antivirus software is installed and that its’ virus database files are up-to-date
5. Maintain regular operating system updates, such as "Windows Update"
posted by Steven Sundermeier | | | | March 15, 2010:
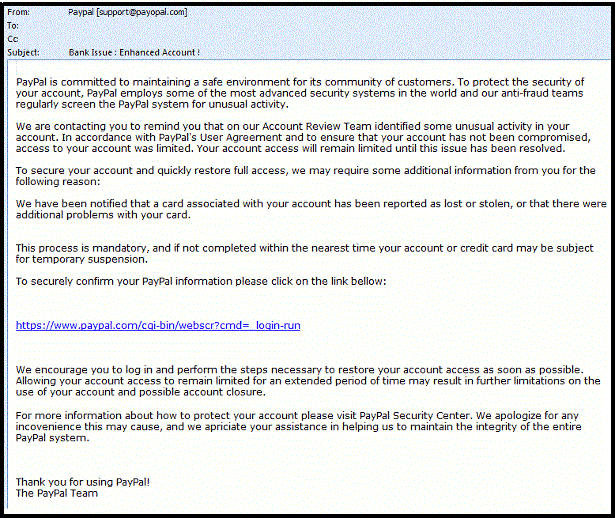
PAYPAL SCAM
By now many users have received a Paypal and/or Ebay phishing scam in their inbox within the past year. However, over the years, these style of phishing attacks have gotten a little more sophisticated. One thing to notice is that (while not perfect) the grammar and punctuation in these emails have gotten better. Another advancement is the more aggressive nature of obtaining the email addresses. For example, the Thirtyseven4 email address (that received the email shown below) is an unused address and only placed on a few websites online. Bots are often used to extract email addresses from webpages in order to conduct targeted attacks.
As always never click on links from within an email. If you have questions about your Paypal account, go to the Paypal site and logon to your account directly. A user clicking on the link in this email would of been redirected to a phishing site located at: h*ttp://apollo1.szv.tsf.hu/grundt**/files/images/***/www.paypal.com/us/webscr.html?cmd=_login-run?cmd=_login-run
posted by Steven Sundermeier
| | | | March 11, 2010

I just got handed a copy of The Medina Sun News this morning and read an article they wrote about us, what a nice way to start the morning. The article was titled, “Company dedicates itself to healthy surfing” and detailed a little about our business and our product, as well as, highlighting our slogan “Protected with Purpose”- a slogan we selected as we dedicate ourselves to raising the awareness and attempting to fix the problems with the child s.ex trade industry throughout the world.
While I'm proud (and humbled!) to say Thirtyseven4 Antivirus is now protecting computers nationwide and beyond, I greatly value the support we have received from within our local community. Thank you!
posted by Steven Sundermeier | | | | March 8, 2010:
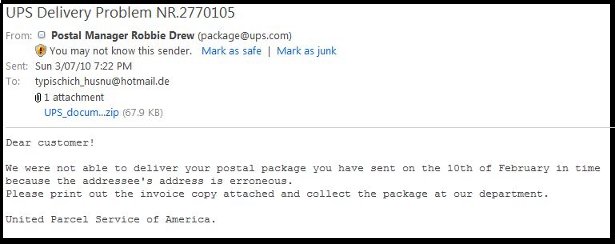
UPS DELIVERY
A new round of emails, like the one shown below (detected as Trojan.Oficla.m), that appear to be coming from the United Parcel Service of America (UPS) have been observed. Instead of receiving the stated invoice copy of your undeliverable package, users who unknowingly open the attachment will be executing malicious code. If you receive a message like this or ones similar, do not open it. Similar messages have been seen exploiting Fedex, USPS, and DHL as well.
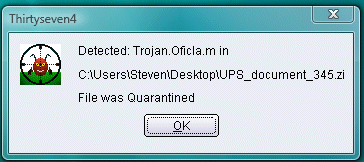
posted by Steven Sundermeier | | | | March 4, 2010
CAUTION: F1
According to a Microsoft blog, Microsoft is investigating a newly discovered vulnerability where users running Windows XP are at risk if they should land on a maliciously crafted website (that exploits this new vulnerability) and inadvertently press the F1 key on the keyboard. Users who fall victim to this new tactic could allow an attacker to run code of his/her own choice.
Users are advised NOT to hit the F1 key if prompted to do so by a visited website. If you should come across such a website, please contact our lab immediately at virus@thirtyseven4.com.
posted by Steven Sundermeier | | | | March 2, 2010
SKYPE: UPDATE REGISTRY
With millions of users and businesses standardizing on Skype for their Instant Messaging software of choice or for telecommunication purposes (to cut local and long distance phone costs), messages like the above are being reported in greater number. These type of messages lots of time bypass security efforts of organizations and make such organizations and its employee's vulnerable to the risks these messages may cause.
In this example (a screen shot is shown below), the following Skype message will appear suddenly and without warning. The message itself claims that vulnerabilities have been detected on your system, and directs you to a displayed website link to get the required update to patch your system. Users who unknowingly click on the link will be directed to an online web scanner for rogueware and will then get redirected to another site (https://cart.secure******tore.com/secureorder/s**reg.php) where they are prompted to purchase software that will repair the detected vulnerabilities.
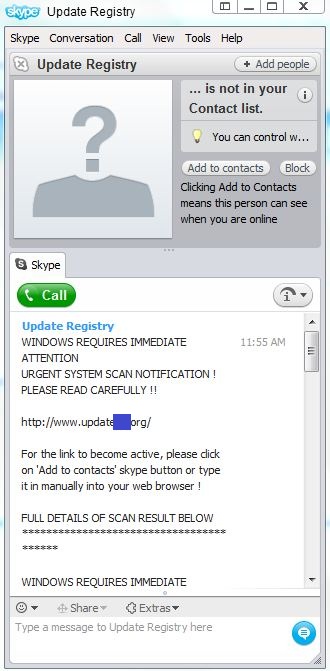
Shortly after writing this blog, my team intercepted more Skype messages just like the above except with varying download links.
posted by Steven Sundermeier | | | | February 26, 2010
GONE PHISHIN', SINCERELY UNCLE SAM
Caution: With tax season upon us again, as expected, a new surge of phishing scams targeting tax preparations, e-filing and the IRS are being widely reported. As with any unsolicited email message, we highly recommend you delete such messages immediately. And while the email or instant message communication (containing a stern warning from the IRS) may stop your heart momentarily: Relax, remove your hand from the mouse, and breathe easier knowing that the IRS will not communicate such responses with you directly over email. Easy remedy - Delete.
posted by Steven Sundermeier | | | | February 23, 2010
YOUR COMPUTER IS INFECTED -- UPDATE NOW
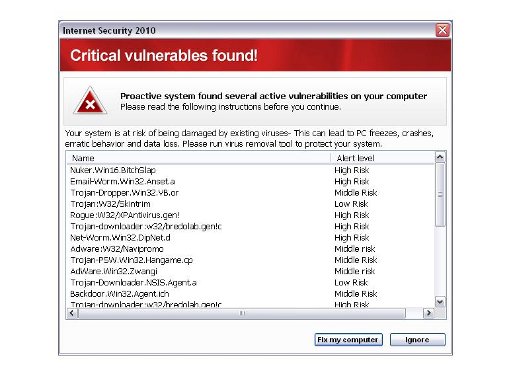
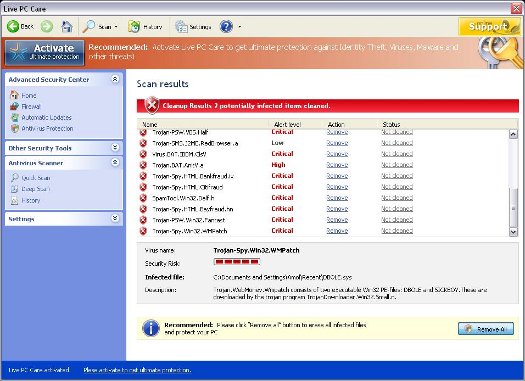
Last month we did a press release on cybercriminals using rogueware to exploit the Haiti relief effort. Since then many people have shared with me that they too have fallen victim to rogueware (for those who don't know, rogueware is a form of software that intentionally deceives users into paying for phony virus removal software by claiming their computer is infected). And while there are countless flavors and variants of rogueware out there, I'm getting requests to post a few example screen shots. To all of you, your desired screen shots are displayed below. You can also check out the description for Trojan.Fakescan.rsm, it contains screen shots of a piece of rogueware named 'Your PC Protector'.
Rogueware is widely used by cybercriminals today to extort your money and this form of malware remains a very serious threat to Internet users. I'd like to say all the frightening stories I've heard came from parents of small children but that's not even close to being the case. The stories are shocking. And for all you Thirtyseven4 Antivirus users, the AntiMalware component within Thirtyseven4 not only detects such rogueware but also does a fantastic job at removing the mess caused by them.
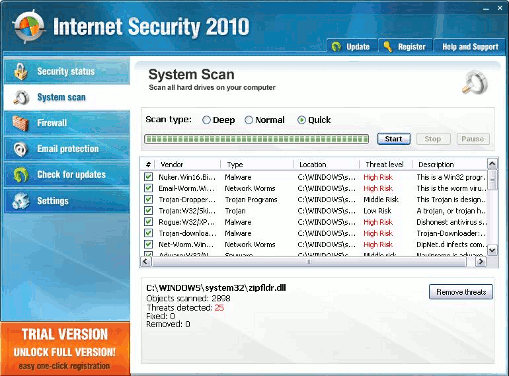
Rogueware: Internet Security 2010
Rogueware: Live PC Care
posted by: Steven Sundermeier | | | | February 18, 2010
THE KING OF POP
We all know by now that virus and malware authors like to exploit the popularity of famous stars for social engineering purposes. It appears that even today, Michael Jackson’s name is still being used for such purposes. We updated today for a new trojan (Trojan.Sasfis.aehs) that downloads a worm that when executed copies itself onto removable drives under the file name, “DVD1.exe”. This file is created in a directory named “MichaelJackson”. A second file is created called “Autorun.inf” to allow for auto execution. The Autorun Protection component within Thirtyseven4 Antivirus automatically safe guards users against such types of automated threats.
It’s my opinion that the naming of the file and directory are in correlation with the recent DVD “This Is It” release earlier this year. And I’m sure that this won’t be the last time we see Michael Jackson’s name, who is arguably the greatest entertainer of all-time, associated with malware.
posted by: Steven Sundermeier | |
|
|  | | | “Delight yourself in the Lord and he will give you the desires of your heart.” Psalm 37:4 | |
|