 |  |  |  | |  | |  | |  |  |  | | Click here for the current Blog | | | | May 24, 2010
SKYPE - SPAM MESSAGES ON THE RISE
Over the weekend there has been a significant increase in the number of unsolicited Instant Messages through Skype. The messages received over the weekend on our baited machines represented a 160% increase in normal activity. Leading the charge for the messages were those alerting users to download critical Windows Updates.
posted by Steven Sundermeier |
 |  | | May 13, 2010 Microsoft Security Bulletins for May 2010 Released
For the month of May, Microsoft has released two bulletins both are rated as “Critical”. We highly recommended you take the necessary steps to apply these bulletins. More information is available at:
http://www.microsoft.com/technet/security/bulletin/ms10-may.mspx
posted by Steven Sundermeier |
 |  |  | | May 12, 2010
UPGRADING TO ADMIN CONSOLE 4.2
As I announced earlier this month, we have released an update to our Admin Console. We’ve received a few questions about upgrading and updated our FAQ support section for the detailed answer. It is a real straightforward process. All a customer has to do is install 4.2 along side 4.1 and in the Administration setting point the old console to the IP Address of the new server and specify the port number, the rest is automated. Once the clients, get updated, you can simply uninstall the older 4.1 version. That’s it.
posted by Steven Sundermeier | | | | May 7, 2010
PDF FUNCTIONALITY EXPLOITED
"Recently, Didier Stevens, a well-known security researcher, demonstrated a social engineering attack, which relies on the "/launch" functionality as described in the PDF specification (ISO PDF 32000-1:2008) under section 12.6.4.5. This is a good example of powerful functionality relied upon by some users that also carries potential risks when used incorrectly by others. The warning message provided in Adobe Reader and Acrobat includes strong wording advising users to only open and execute the file if it comes from a trusted source.*"
A screenshot of the "strong wording" (as noted above) can be seen below:
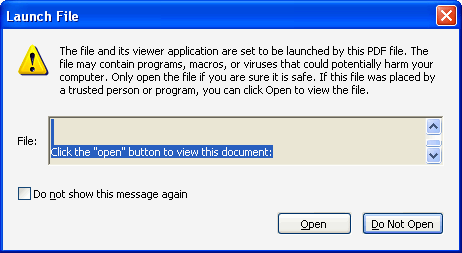
As you may have guessed, it hasn't taken very long for the /launch functionality to be exploited. Our VirusLab has already seen and received maliciously crafted PDF files that capitalize on this functionality. An example file would be "doc.pdf".
Now, taking a look at the screenshot above, the question becomes what would happen if an unknowing users clicks on the "Open" button instead of acknowledging the apparent warning contained within the Launch File message box...let me show show you.
If someone clicks on the Open button, it drops and executes an embedded VBScript and malicious file called "game.exe". See the image below:
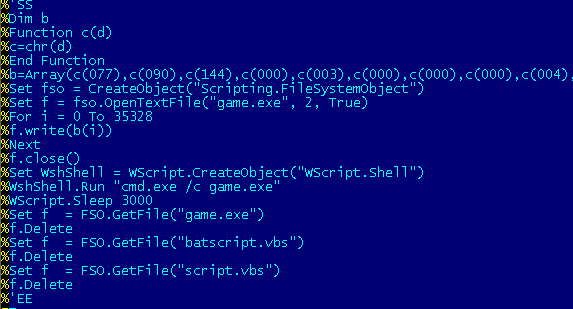
Thirtyseven4 Antivirus has already been updated to detect the threat caused by this PDF. The threat is identified as Exploit.PDF.Pidief and the associated dropped file (game.exe) is identified as Trojan.Agent.pack.
* Information was taken from:
http://blogs.adobe.com/adobereader/2010/04/didier_stevens_launch_function.html
posted by Steven Sundermeier | | | May 3, 2010
Admin Console 4.2 Released - You Spoke, We Listened
I’m very proud to announce the next generation release of our Admin Console. With all the wonderful feedback we have been getting back from school districts and businesses around the nation, we made a decision to escalate the development process to accommodate the requests.
Some of the Admin Console enhancements include:
- Thirtyseven4 Admin Console can now be installed on Windows Vista, Windows 7, Windows 2008 Server and Windows 2008 Server R2.
- Thirtyseven4 Admin Console clients of an existing version can now upgrade to a newer version automatically by simply redirecting the existing version to the newer version.
- Thirtyseven4 Admin Console Client and Server communication will not be blocked by the the Windows Firewall, even if the WIndows Firewall is Turned On.
- Customizable action can now be taken when viruses are detected inside archived files. The following actions can be performed if a virus is detected in an archived file: Delete automatically, Prompt, Report only and Quarantine.
- Thirtyseven4 Admin Console Client Server communication has been enhanced. It will also support a DHCP based setup.
We have also updated our Thirtyseven4 Admin Console with all the features above, as well as with detailed instructions on how to upgrade your Admin Console to Admin Console 4.2. The manual can be downloaded from here.
posted by Steven Sundermeier | |
 |  | | April 30, 2010
Microsoft releases update for Security Bulletin (MS10-025)
As an update to my posting on April 22, 2010, Microsoft has released an update for their Security Bulletin (MS10-025). The update was released on April 27th, 2010. You can read more from:
http://www.microsoft.com/technet/security/bulletin/ms10-apr.mspx
posted by Steven Sundermeier |
|  |  | | April 28, 2010
New Educational Program Released: Help is on the way
I wanted to write a short note this morning concerning our new educational program. Here at Thirtyseven4, we are 100% committed in helping schools. Our hope is that our program will allow smaller schools and larger schools alike address any holes and/or security compromises that budget cuts seem to be forcing.
Check out the custom made security awareness poster to the left of this blog. Scareware remains a top threat to school systems, as well as home users and small businesses. Feel free to request a poster or two for your office or computer lab. |
|
 |  | | posted by Steven Sundermeier |
 |  | | April 26, 2010
Hackers at it again: Old tricks, New search term
Cybercriminals are at it again. Results on a test for last weeks hot news topics have shown that hackers were very quick to capitalize on Mcafee's false positive issue that cause thousands of systems to reboot continually last week (the rebooting was caused by falsely detecting a genuine Windows file 'svchost.exe' as 'W32/Wecorl.a'). By using a technique called Search Engine Optimization (SEO) poisoning, cybercriminals have been successfully able to position malicious websites high in search engine rankings. These malicious websites often redirect to other malicious websites or host malware applications themselves. Many forms of Rogueware and Scareware get inadvertently installed daily by unknowing users this way.
When searching hot new topics, it is always best to go to a reputable news site directly.
posted by Steven Sundermeier |
 |  | | April 22, 2010
Major Revision Upcoming for Microsoft Security Bulletin (MS10-025)
The Microsoft Security Bulletin MS10-025 has been updated. When originally released, as part of the Microsoft security bulletin for April 2010, it contained serious quality issues. The bulletin was pulled by Microsoft soon after they became aware of the problem. According to Microsoft, an update will be released once complete testing has been done. Basically, the original security bulletin didn't do anything to protect systems from the vulnerabilities set forth in the bulletin. Microsoft had rated the bulletin "critical" due to the "Remote Code Execution" vulnerability affecting MS Windows 2000 Server running Windows Media Services.
You can visit the Microsoft website regarding this bulletin by clicking here.
posted by Thirtyseven4 Viruslab |
 |  |  | | April 16, 2010:
Nigerian Scam - "$500,000 is waiting"
These Nigerian style scams come in a variety of shapes and sizes and I could probably write about a different one every day for the next few months. Anyhow, last month I wrote a blog about a similar scam (that one about Winning the Mega Jackpot sponsored by Microsoft)- this time I was selected as a random receipt of $500,000.00 from the United Nations Compensation Unit. As with most Nigerian style scams, the email seeks a reply from you with your personal data included.
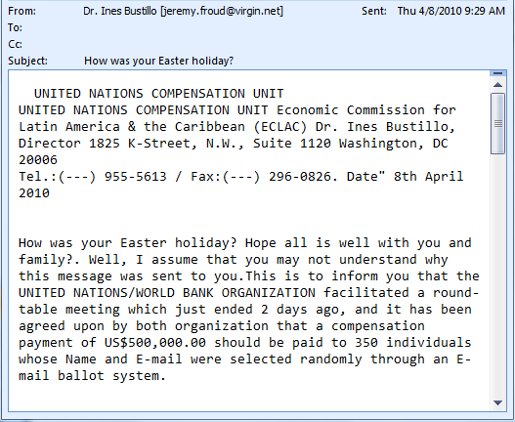
If you should receive an email like this- delete it right away. It's a scam.
posted by Steven Sundermeier | | | | April 14, 2010
REMEMBER NHU - “Thank You”
I wanted to take a break this morning from posting a security blog to write a special “thank you” to all the home office users, small businesses, schools, colleges and others who have put their trust in Thirtyseven4 Antivirus. As many of you know, since the very beginning, Thirtyseven4, LLC has partnered with the non-profit organization, Remember Nhu- and a portion of each sale goes to their cause. It is also where our slogan ‘Protected with Purpose’ comes from. Well, the founder’s of the organization Carl and Laurie have just returned from their latest trip to Asia and have been gracious enough to provide me updated pictures. While I can’t post them all, I thought I’d include a few...


posted by Steven Sundermeier
|
 |  | | April 8, 2010
GOOGLE OR MICROSOFT - Malware Authors Deceive with Both
Having a hard time deciding whether to use the search engine powered by Microsoft or Google? As it has been well noted in my past blogs, cybercriminals will attempt to exploit web searches done on any search engine. However, what I've found interesting in a recent virus description we posted last week, is that appears malware authors are having a tough time deciding what file names would have a larger impact for deception- ones associated with Google or ones associated with Microsoft.
Take a look at Trojan.Buzus.dckk. Upon execution, it creates a copy of itself locally as "GoogleUpdates.exe", yet on located and accessible removable drives it creates a copy of itself under the file name "redmond.exe" (Redmond, WA is the headquarters of Microsoft Corporation). Additionally, a file is created locally called "lsass.exe". Typically, in a Windows environment, the lsass.exe process is responsible for management of local security authority domain authentication and Active Directory management.
So what's it going to be...Google or Microsoft?
posted by Steven Sundermeier |
 |  |  | | Date: April 5, 2010
"TWEETS TWEETS" - TRENDING TOPICS DANGER
As it has been reported before here and on other sites, social networking sites are a very popular avenue for cybercriminals to attract new victims. Here at Thirtyseven4, we're continually scanning these sites for new schemes and vulnerabilities to better protect and serve our customers.
A common place for such attacks is on twitter. Without much effort you can locate a twitter profile posting tweets with no text just miscellaneous links. Typically, the links are (unnoticeably) long due to the embedding of almost all the day's "TRENDING TOPICS" (trending topics scroll off the top of twitter.com homepage: see the example screen below snapped on April 2nd).
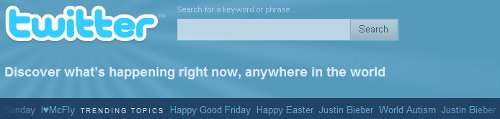
To the eye, the links themselves are shortened as not to raise a red flag and appear to be news links pertaining to one of the hot topics. If such a link gets clicked 99% of the time some sort of malicious activity can be expected.
In a real world example, a recent search was done for one of the twitter trending topics. As expected, a twitter profile was easily located who posted messages as described above. Proceeding in a controlled environment, when a member of our virus lab clicked on the short URL it directed them to a website that took a long time to load. Eventually the browser appeared with a black background with no text and only the image below.
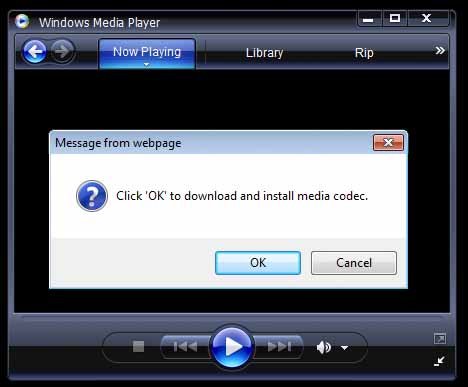
As the image shows, it prompted to download the 'media codec plugin' to show the so-called streaming video. When "Ok" was selected, surprise surprise...down came a malicious program.
Extreme caution is recommended when doing searching for hot new topics, whether you're doing it on twitter, another social networking site, or a search engine.
It’s important to note that files of this nature that may get unknowingly downloaded through twitter or simailr websites are being detected by Thirtyseven4's DNAScan Technology as malicious applications.
posted by Steven Sundermeier | | | Archived Blogs
June - July 2010
April - May 2010
January - March 2010 | |
|
|  | | | “Delight yourself in the Lord and he will give you the desires of your heart.” Psalm 37:4 | |
|