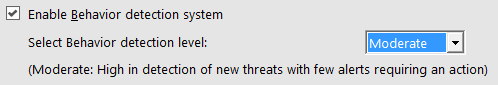
Behavior Detection System- The Thirtyseven4 DNA Scan Engine has been thoroughly and carefully trained with Machine Learning abilities to recognize threats as they arise, allowing the scan engine to proactively and aggressively detect threats automatically, which has lead to industry leading detection rates and a smaller engine size. Click here for more technical details.
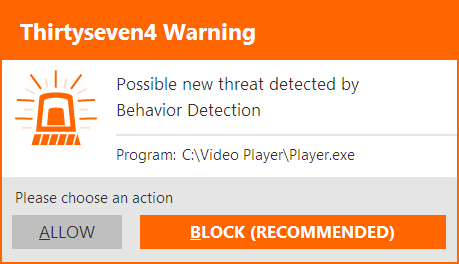
AntiMalware - Thirtyseven4 Antivirus is one of a very select few antivirus products in the world that not only offer detection and prevention against today’s Malware but also offers complete Malware removal. The Thirtyseven4 AntiMalware module eliminates the need for other 3rd party security applications.-
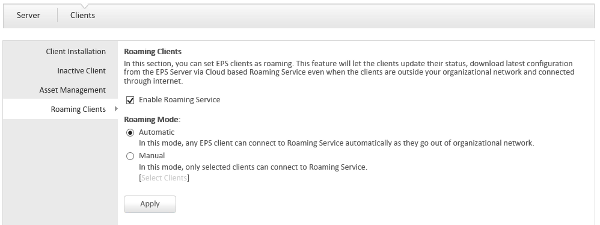
ENHANCED Thirtyseven4 EPS Cloud-Platform - By connecting to our Cloud platform and configuring your Roaming Clients, Administrators can now deploy and manage offsite (away from the network) systems as if they were on the network. Roaming Clients can be pushed configuration changes, scans, virus definition updates, send malware statistics and module reports back to the Console, etc.
Web Browser Sandbox - This powerful browser sandbox ensures that any browser-exploiting threats are automatically contained and are unable to affect your system by creating a virtual browsing environment, protecting your system against zero-day malware attacks, compromised websites with ‘drive-by’ malware downloads and keyloggers. Websites protected by Sandbox browsing will be outlined with a green box (see below).
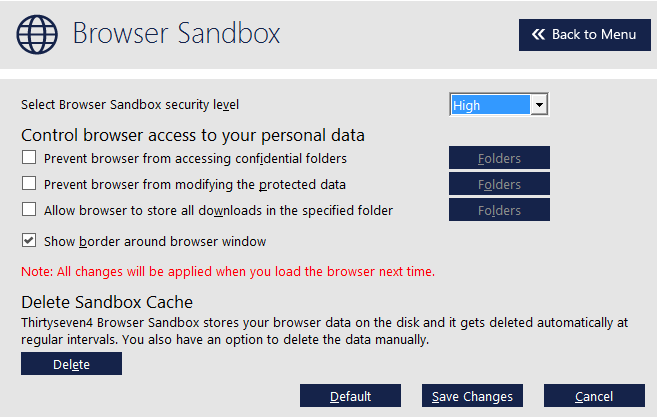
Browsing Protection - The Browsing Protection features our new integrated Cloud-based technology blocking thousands upon thousands of malicious ip addresses, domains and sub-domains daily, thus protecting your computer from dangerous and malicious websites, allowing for a safe browsing experience.
Phishing Protection - The Phishing Protection feature prohibits access to fraudulent websites
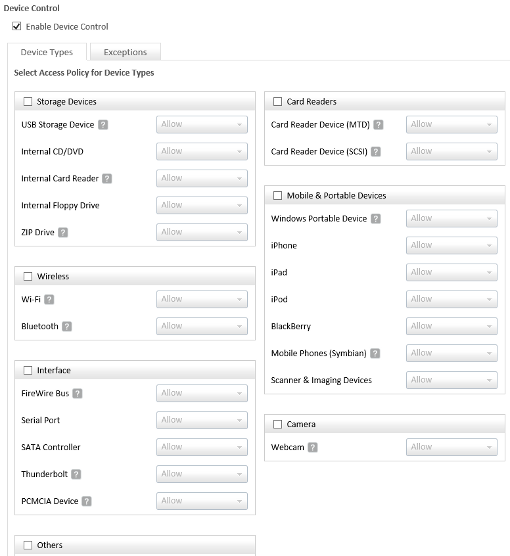
Advanced Device Control- With Advanced Device Control, users can now control over 25 devices with different Access Control settings such as:
- Block Access
- Allow Access
- Read Only Access.
You can also configure different access policies for the following types of devices:
- Storage devices (USB Storage Devices, Internal CD/DVD, Internal Card Reader, Internal Floppy Drive, ZIP Drive)
- Card Reader Devices (MTD, SCSI)
- Wireless devices (Wi-Fi, Bluetooth)
- Mobiles (iPhone, Smartphone, Blackberry, iPad, iPod)
- Camera (Webcam, Digital Camera)
- Local Printers
- Network Share
- Windows Portable Devices
Data Loss Prevention (DLP) - With DLP, users can monitor & block potentially sensitive data from leaving an organization through various channels like:
- Removable Devices
- Network Share
- Clipboard
- Print screen
- Applications & Online Services (such as Web Browsers, Email Clients, etc.)
In addition, users can configure the following types of data that can be monitored:
- Different files (e.g. Office files, Image files, etc.)
- Confidential information (Credit Card Numbers, etc.)
- User Defined Data
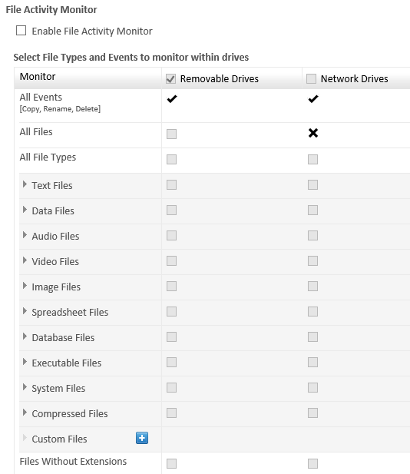
File Activity Monitor - Users will now be able to monitor file activities such as file copy, rename and delete across all systems where the Thirtyseven4 EPS Client is present:
- Local drives
- Removable drives
- Network drives
This feature was developed to assist auditing and forensic activities for internal and external threats.
Asset Management - This feature will help Network Administrators track Hardware and Software changes in the network (ie. audting purposes). The module works by collecting the following information about the endpoints:
- System Information like Operating System details, Local user accounts, System Turn ON and Shutdown time, etc.
- Hardware Information like System Manufacturer, Motherboard, Processor, RAM, Storage, Video Adapter, Sound Adapter, Optical Drive, N/W Adapters, Printers, etc.
- Software Installed
- Updates Installed
This feature also keeps track of software and hardware changes happening on the endpoints. For e.g. Processor changed, RAM changed, some software installed/uninstalled.
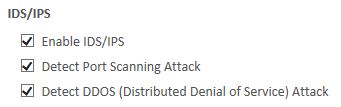
IDS/IPS - The Thirtyseven4 Intrusion Detection System & Intrusion Prevention System uses a signature based detection method, as it has embedded rules to detect various attacks & vulnerability in the system. It scans network traffic for malicious packets and if any of the packets signatures match a Thirtyseven4 predefined IDS rule then these packets will be discarded and won't reach your computer.
IDS/IPS also now includes:
a. Port Scanning to block intruder attempts to check open ports of a system within your organization.
b. Distributed Denial of Service (DDOS) Attack Prevention to detect and prevent denial of service attack.
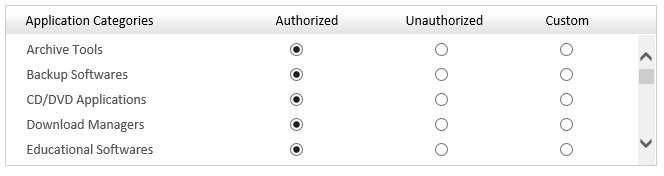
Application Control - Provides Network Administrators the opportunity to actively scan and detect and proactively block unauthorized applications for being installed within their environments
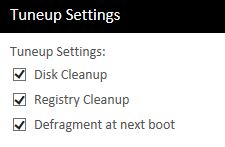
Tuneup - Improves performance of client systems by performing Network-wide periodic PC Tuneup Scans. Tuneup settings include:
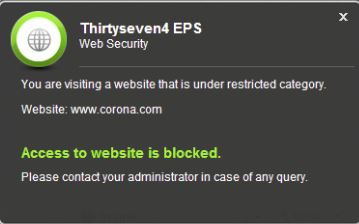
Web Security - Client level Content Filtering, controlling the web access of your clients based on website categories, such as Social Networking, Games, Alcohol, etc.
Email Security- The Email Security features within the Thirtyseven4 Endpoint Security Console allows clients to be fully protected against of all today’s email-borne vulnerabilities, exploits, malware, virus and worm threats. The security component also provides the opportunity to proactively block attachments based on file types.
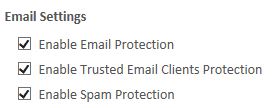
Full Spam Protection is now offered as part of the Endpoint Security offering. The Spam Protection controls are highly flexible for white list, black list and other configurations.
Vulnerability Scanning- This feature allows a user to scan for known vulnerabilities of installed applications of various vendors such as Adobe, Apple, Microsoft, Mozilla, Oracle, etc.
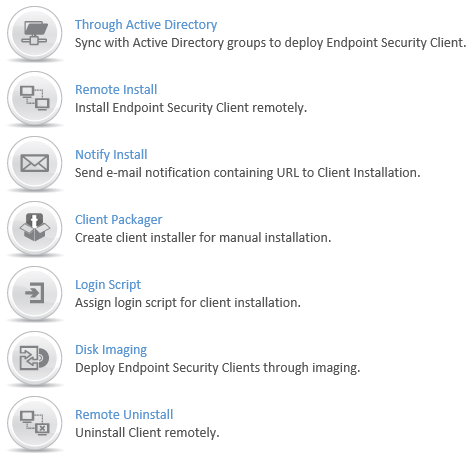
Multiple Deployment Options-
  Upgrading Instructions Endpoint Security Console Comparisons Upgrading Instructions Endpoint Security Console Comparisons |