The Behavior Detection System (BDS) is a dynamic-based scanner introduced in the Thirtyseven4 2014 Product Series (Endpoint Security 5.3 & Thirtyseven4 Antivirus 2014). On the local client, the module can be accessed by clicking the ‘Files & Folder’ option on the main dashboard of Thirtyseven4 and looking under the ‘Advanced DNAScan’ settings.
A sample of the BDS options available:
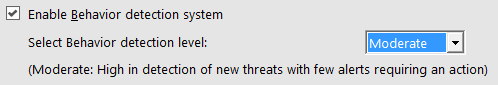
The BDS is a powerful and effective system that constantly observes all application behaviors and immediately alerts users if suspicious or malicious application behavior is detected using industry leading machine-learned technologies. It also is developed to crosscheck behaviors on-the-fly against known malware. The integrated BDS prevents dangerous and widespread threats (i.e. Cyptolocker) from penetrating a system.
Because of complex and continually evolving malware threats like CyptoLocker, conventional antivirus scanners are becoming less effective and the need for more proactive measures is great. Let’s take a look at how Thirtyseven4’s Behavior Detection System meets and exceeds that need.
Here’s how the Behavior Detection System works (CyptoLocker example):
A Thirtyseven4 Antivirus 2014 user downloads and attempts to run a file they believe is harmless, and the file in this example is a brand new variant of CyptoLocker (with no known industry-wide signature detection). The file is executed.
Upon running the file, the Thirtyseven4 BDS immediately flags the file as suspicious.
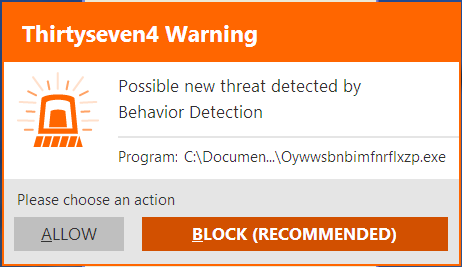
Thirtyseven4 blocks the file from executing and moves the suspicious file into Quarantine.
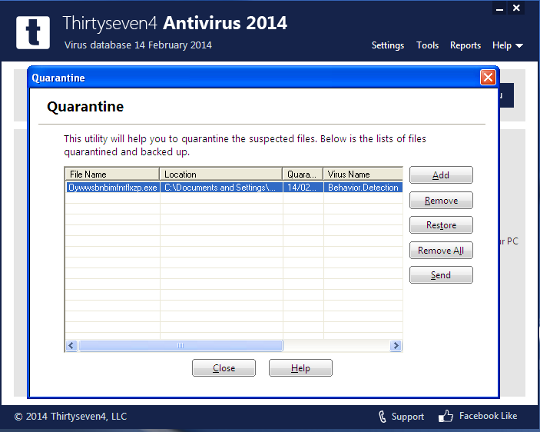
Behind the scenes and without interaction from the end user, the Quarantine directory is emailed off to the Thirtyseven4 Viruslab Team for immediate analysis. Upon receiving the suspicious file, the file is immediately analyzed and a signature is placed on the file and added to the next daily update pattern. In this case the signature name is ‘Trojan.Crilock.A’. This entire process takes less than 24 hours.
If the user would encounter this malware again with the new update signatures in place, the Thirtyseven4 Virus Protection (real-time) module would immediately intercept it upon Files Access Call.
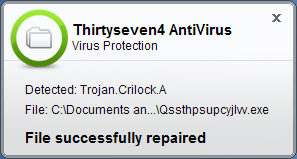
Below is an example of the Thirtyseven4 Virus Scanner (On-Demand) detecting the file:
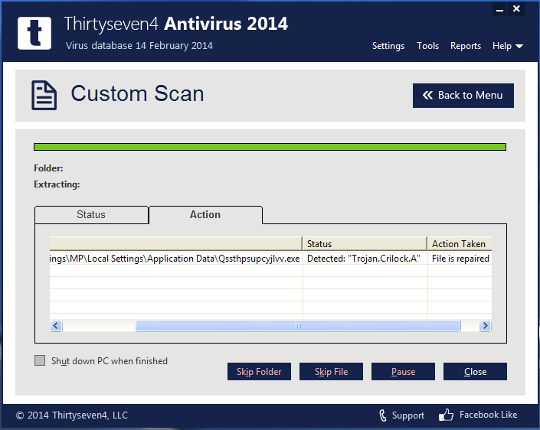
So what caused the Thirtyseven4 Behavior Detection to flag the file as suspicious initially?
As you can see from the Behavior Detection Report below, our proactive scanner analyzed the file on-the-fly and determined that the file was attempting to (a) Make a random copy of itself and (b) Attempted to modify sensitive system resources.
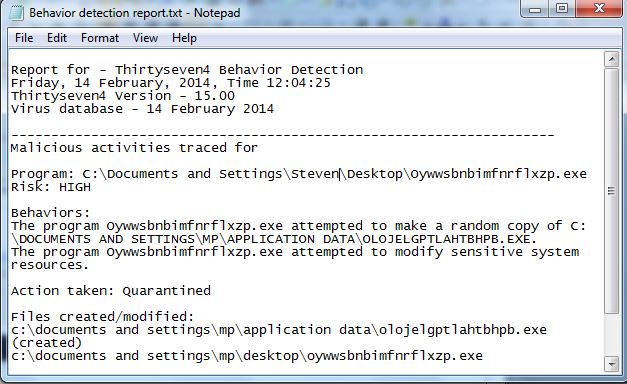
Because of the Behavior Detection System, this Thirtyseven4 users system is safe and was not infected. If you are not yet a Thirtyseven4 customer, we highly recommend downloading a trial license and evaluating Thirtyseven4 Antivirus 2014. |