What is Worm.Vobfus?
By definition, Worm Vobfus fits into the Worm category due to its ability to spread via network drives and removable drives and for its ability to download and execute arbitrary files. The name Vobfus comes from the combination of words V(isual Basic) + Obfus(cator).
The Worm Vobfus family of worms are know for their polymorphic capabilities [the ability to change itself to avoid detection with each new execution] and for their aggressive download and propagation routines.
What computer language is Worm.Vobfus written in?
Worm Vobfus is written in Visual Basic. Visual Basic is the framework or compiler from Microsoft that is similar to other compilers like Visual C++, Delphi from Borland. Visual Basic was popular among developers during the late 90s as it is an easy program to learn and develop on. Over the last few years, Visual Basic has regained popularity among cybercriminals due to code obfuscation, a technique used by attackers to deliberately modify their code complicating analysis for virus researchers and to conceal the malicious purposes the worm. It also uses various encryption techniques like RC4. Visual Basic code is either in Native code (processors could directly understand) or intermediate code that is understood by a VB Virtual Machine, this adds one more layer of obfuscation.
How does Worm.Vobfus avoid detection?
Worm.Vobfus variants can easily be modified by adding garbage code at every iteration (example shown below) to create new MD5 hashes to avoid detection or to allow for modifications in the code to generate new variants. Due to its effective code obfuscation techniques, it can make on-the-fly detection for new variants difficult to detect.
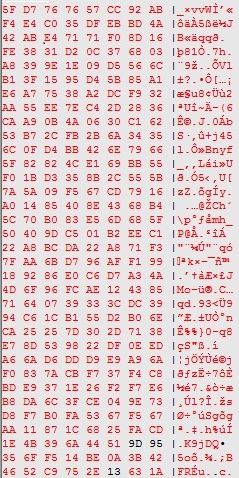
(the picture above shows an example of Vobfus encrypted code that will get decrypted and executed by the malware upon each execution. The technique and code can vary according to the Vobfus variant)
Is Worm.Vobfus a new worm? Is it unique?
Vobfus belongs to a family of obfuscated worms that has been seen around since 2009. However, Vobfus only began exploiting the shortcut vulnerability towards the end of 2010. The first variant we updated for that had exploited the shortcut vulnerability was Worm.Vobfus.AC6.
Vobfus uses various propagation techniques that can be used by other worms as well. The highly publicized Stuxnet creation and even Sality (according to various reports) also use the LNK vulnerability and removable drives to spread. So while not unique in the functionality it contains, using similar techniques does not make it a copycat or deviation of any existing malware. The worm Vobfus is unique.
Do you have an estimate on how many systems are infected with Worm.Vobfus?
At the time of this virus description, Thirtyseven4 has blocked/repaired more than 200,000 machines from Vobfus related infections in the last three months. And as noted in our Press Release, 39% of inquiries into our Virus/Support Teams involved questions around the Vobfus family. Thirtyseven4 is regularly receiving new variants.
How does Worm.Vobfus spread?
Worm.Vobfus variants spread by dropping copies of itself, at frequent time intervals, onto all removable drives and mapped network drives connected to the infected system. The worm also exploits the Windows OS Autorun feature so that those dropped files can get auto-executed, this is done by the creation of an Autorun.inf on the infected system.
In addition to the techniques above, Worm.Vobfus variants can also arrive on a system by visiting a website containing malicious code or can get dropped or downloaded by other malware families.
It can also spread from system to system through a known Microsoft vulnerability and we have reports of Worm.Vobfus variants arriving on a system via scams/links on social networking sites.
Dropped copies of itself on the root folder of network and removable drives will have the following names-
passwords.exe
porn.exe
secret.exe
sexy.exe
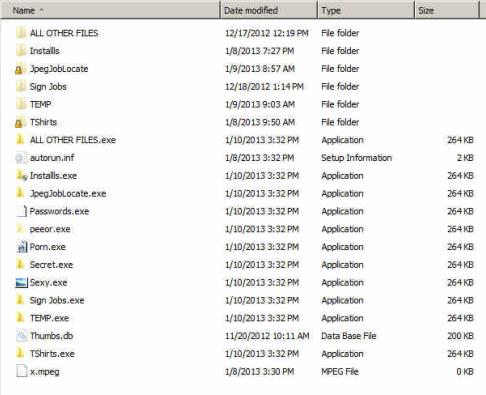
(Vobus infections hide the extension of files and create its malicious files having the Windows folder icon, image icon, etc. in order to disguise itself and trick users, as pictured above)
What happens when Worm.Vobfus executes?
When Worm.Vobfus is executed, it will drop a copy of itself as an executable file (EXE) in the %USERPROFILE% folder using a random file name, for example "zuaixap.exe" or "nuaeku.exe". Additionally, it may also drop a polymorphic file in the %USERPROFILE% folder using a random file name as well.
Worm.Vobfus variants change the affected folders attributes to Hidden and System in order to avoid detection and consequent removal.
It will then modify the following registry entry to ensure that the copy of itself will execute at each Windows start:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"yuuel"="%USERPROFILE%\yuuel.exe /z"
Next, the worm connects to several bad websites waiting for commands from remote attackers. Examples include (websites vary between variants):
hxxp://aact.ru/f/mixc.exe
hxxp://cvfl.su/l/sc.exe
hxxp://cvfl/l/3580c.exe
Typical communication between an infected system and a malicious server would result in packets being sent that contain additional URL’s that the Vobfus variant will access in order to download files of the attackers choice
Lastly, Worm.Vobfus variants hook certain Application Programming Interfaces (APIs) preventing applications such as Task Manager and Process Explorer from terminating their malicious routines.
Do Worm.Vobfus infected systems automatically become “zombie” systems?
At the time of this description, we haven’t observed such behavior relating to the Vobfus family. The primary purpose of the Vobus family of malware is to act as a vehicle to download other malware. The downloaded malware could then join the system to be part of Bot network, and exposing the machine to become accessible and under the control of a Bot herder.
How can I safeguard against Worm.Vobfus?
Thirtyseven4 suggests the following preventive measures to reduce the risked posed by the Worm.Vobfus family:
1. Disable the Autorun functionality
a. Disable Autorun on USB drives - more information on that
b. Disable Autoplay using Group Policy Object (GPO) within your environment - more information on that
c. Disable the Autorun functionality using Registry Editor - more information on that
2. Keep operating systems and other installed software patched against known vulnerabilities
3. Limit access to Shared folders and removable drives
4. Be diligent when opening attachments
5. Be aware of phishing schemes, and avoid clicking on links within emails, instant messages or on social networking sites
6. Install antivirus software, making sure it remains up-to-date and scanned at regular intervals
Am I protected against Worm.Vobfus with Thirtyseven4 Antivirus?
Thirtyseven4’s flagship solution, Thirtyseven4 Antivirus is routinely updated against the latest Worm.Vobfus variants and also incorporates advanced generic detection routines via its DNA Scan for the Vobfus family. The DNA Scanner offers proactive protection against such threats. New threats are proactively detected flagged as ‘Suspicious’.
Known Vobus variants are currently detected and removed via the Thirtyseven4 Scanner and/or its real-time time scanner Virus Protection under the signatures: Worm.Vobfus.KL3, Worm.Vobfus.NM3, Worm.Vobfus.DF3 and TrojanPWS.Zbot.Gen. (this will likely be added to as more variants are detected)
All the malicious websites (including the ones above) that the Worm.Vobfus family connects to are covered and blocked by Thirtyseven4’s Browser Protection.
Additionally, Autorun Protection is a core a feature within Thirtyseven4 solutions that proactively cripples the Autorun feature on external drives and devices, thus proactively blocking all know and unknown threats from spreading onto another system or network via a removable drive or device. |