Here is an example email:
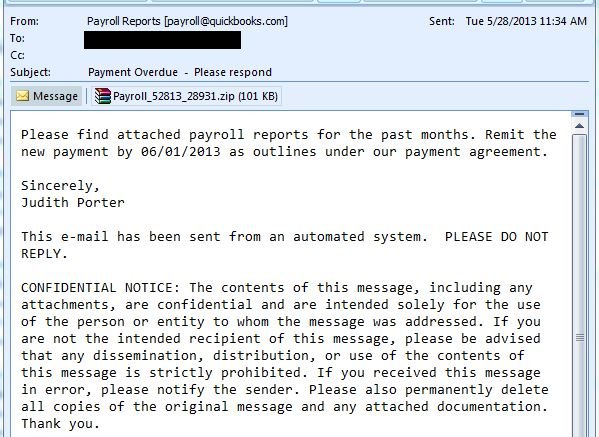
If the attachment is executed, the unknowing user’s machine gets infected with a Trojan identified by Thirtyseven4 Antivirus as “TrojanPSW.Tepfer.lfl“.
Upon analysis of the Trojan, we have observed that the file drops files at the following locations-
%AppData%\[randome_name folder]\[randome_name].exe {polymorphic file}
The dropped files by TrojanPSW.Tepfer are polymorphic in nature (meaning every time you visit the same link you will get a different file).
In addition to updating the Thirtyseven4 Antivirus virus scanner for these threats and future similar threats, the Thirtyseven4 Browser Protection module will be immediately updated to block any future websites should this Trojan start attempting to reach malicious websites.
Please note: That since the time of this writing, our Viruslab has intercepted several other variations ironically spreading under the Quickbooks name. Most of them will be detected within the TrojanPSW.Tepfer family and the others will be detected as “TrojanSpy.Zbot.lvw”.
|