Trojan.Crilock.A is ransomware that spread using social engineering tricks via social networking site and email attachments. It is very similar to the infamous FBI Moneypak virus.
How does CryptoLocker work?
When CryptoLocker executes, it copies itself to the root directory of the %APPDATA% folder with files named {GUID}.exe- these files are created with hidden attributes.
For example, C:\Documents and Settings\Administrator\Application Data\{71257279-042B-371D-A1D3-FBF8D2FADFFA}.exe
Trojan.Crilock.A uses the RSA algorithm with a 2048 bit key. It communicates with servers at random whose names are generated using the Domain Name Generation (DGA) algorithm. Once communication is successful, the server generates a pair of public and private keys for the machine of the targeted user. The private key is kept on the server for the next 72 hours. The public key is sent to the malware running on the user’s machine using a secure communication, stored under the HKCU registry key as shown in the following image:
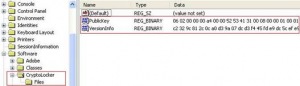
Next, the malware will begin looking for the files extension mentioned in the following list below:
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.pdf, *.mdf, *.dbf, *.psd, *.pdd, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c
From the thorough list above, it can be observed that the malware targets all users who have important information stored on their machine and wanting to restore access back.
The list of the infected documents is kept under:
HKEY_CURRENT_USER\Software\CryptoLocker\Files
This list is kept to avoid multiple encryption’s.
The CryptoLocker ransomware is shown below:
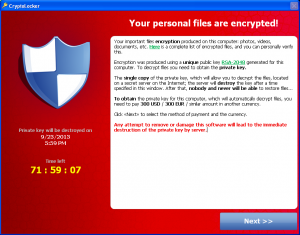
CryptoLocker provides three ways of making payment (via MoneyPak, Ukash and Bitcoin). The amount is equivalent to $300 USD, and the amount can be paid in 15 different currencies. It is important to note that Bitcoin is being increasingly used by malware authors.
It is extremely difficult to recover encrypted files once they are encrypted with RSA algorithm, until we have the private key.
How can you detect CryptoLocker?
Thirtyseven4 Antivirus detects this family of ransomware as Trojan.Crilock.A.
Recommended Security Measures
Taking the following security measures would help reduce the risk of such a malware attack like CyptoLocker:
- Ensure that all important software on your machine, such as the Operating System, Adobe Reader, Microsoft Office, and internet browsers (to name a few) are patched and up-to-date.
- Keep your machine’s security software up-to-date.
- Avoid clicking URLs and opening unsolicited email attachments, particularly from unknown sources.
- Be careful while using removal devices such as pen drives, external hard disks, etc. These devices may be coming from machines not protected by updated security software.
- Always keep a backup of all your important documents using a reliable backup software.
|