With tomorrow (Black Friday) being the largest shopping day of the year, e-mail scammers are out in full force trying to entice users with false Black Friday Deals, and dupe users into thinking there were issues with their recent credit card and banking transactions. Below is just one example seen yesterday involving KeyBank (we have seen others involving US Bank, Chase, Bank of America and other international banks).
From: Junior_McIntosh@KeyBank.com
Subject line: You have received a secure message
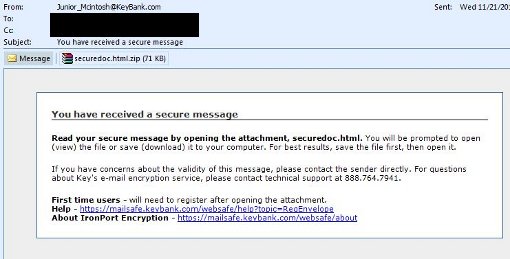
Other Examples:
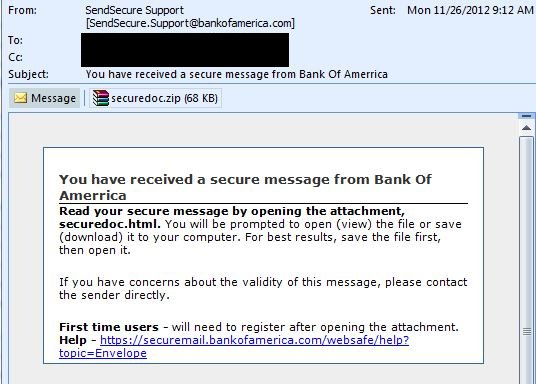
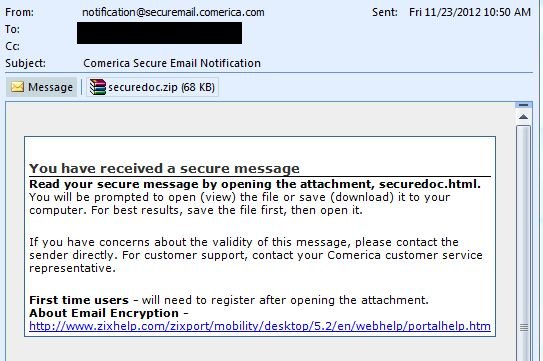
If the user would open and run the attachment as instructed. The executable will drop the following files:
%userprofile%\[randome-name].exe
%appdata%\[randome-name]\[randome-name].exe [polymorphic sample]
It will then modify the following registry keys-
[1] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Value Name : {DD369C45-40D3-AD42-A07B-23D9844D00CB}
Value Data : "%appdata%\Qujoz\guevb.exe"
[2] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Value Name : wiptutogdaxh
Value Data : %userprofile%\wiptutogdaxh.exe
It will then communicate to the following domains to download and install Scareware on to the system:
v-7xxx2-74-152.unman-vds.internap-nyc.nfoservers.com
crs.ultxxxdns.net
200.xxx.130.72
pop09.xxxhlink.net
cms01.xxx.oakland.edu
213.202.xx.212
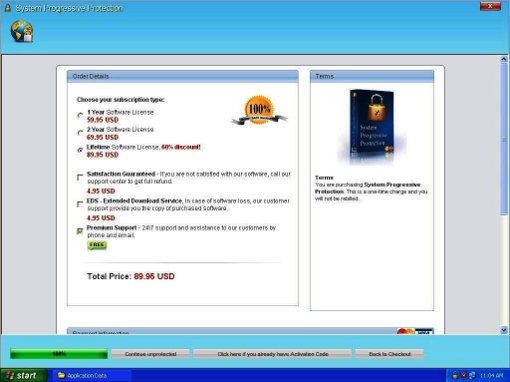
A Fake Security Application on to the system. In this case, the Fake Application is called, “System Progressive Protection”. See below:
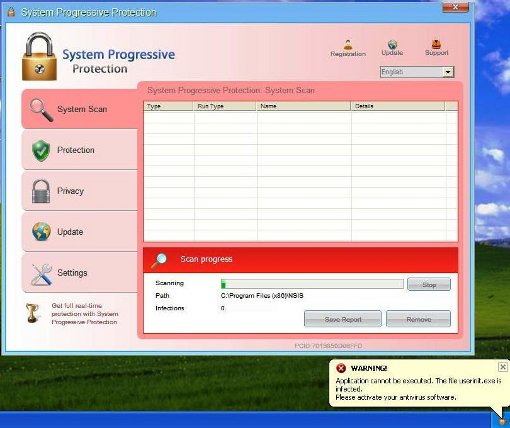
The Fake Application will remain and be very problematic to remove until the user goes out and purchases the Fake Software.
Thirtyseven4 detects this file as FraudTool.SysTool.2011, and our free security tools will remove this threat. |