Frozen) on her adventure to locate runaway sister Elsa. In fact, given the sub-zero temperatures we’ve been experiencing, I‘m positive you wouldn’t even see me on the sidelines cheering for her and Kristoff during their adventures.
With everything seeming to freeze around me (isn’t it frustrating when soda cans and water bottles freeze and explode in the garage fridge!), I’d like to speak on an area that is HEATING UP, and that unfortunately is ransomware infections.
Ransomware is a form of malware developed to encrypt (prohibit access to) files on a computer with the sole intent of extorting money from its victims (paying a ransom to recover encrypted files). Generally speaking there are two main classifications for ransomware, Encryptor (encrypts all important files and demands a ransom to decrypt files) and Screen Locker (locks an infected system, preventing proper access until a ransom is paid). Most of the latest strains that our Thirtyseven4 Labs are observing fall under the Encryptor classification. The top ransomware threats include, Cryptorbit, Cryptolocker, CryptoWall, PornoBlocker, ZedoPoo. My hope is that none of these are familiar to you…
Malware writing is big business for cybercriminals, and ransomware creators are fully aware that millions of dollars were extorted in 2014 from helpless victims through this style of malware. As noted above, the general premise of ransomware is to lock users out of their personal data, and then demand payment to recover the locked information. The payment is usually requested in the form of direct credit card payments or via Bitcoins (online payment currency). Ransomware targets file types that are most valuable to the user: documents, images, photos, etc. Think about it- what price tag would you place on recovering a decade worth of digital photos of your babies growing up, or recovering all of your businesses critical tax documents?
Making matters worse, the frequency and sophistication of ransomware has increasingly grown, and such attacks have now been perfected to penetrate even the most advanced networks. Over the last 30 days (January 2015), my Thirtyseven4 Viruslab Team has updated for more than 300 variations of ransomware. Given the severity of ransomware and the alterations being made on each new variation (enough to evade signature-based detection), conventional virus scanning for such malware types no longer cuts it. Ransomware was the driving force behind our new cutting edge Behavior Detection System technology, which proactively scans for ransomware-style characteristics and behaviors in real-time. Given the noted advanced heuristic-based technology, we are very proud to claim a near 100% success rate against these threats.
Here are some real world ransomware statistics, based on actual intercepted and prevented infections for Thirtyseven4 Endpoint Security users for January 2015.
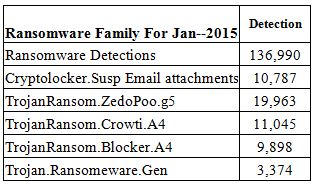
“Ransomware Detections” reflects the total number of ransomware detections for January 2015. In other words, Thirtyseven4 proactively prevented 136,990 infections last month. “Cryptolocker.Susp Email attachments” is the number of malicious emails stopped by Thirtyseven4 Email Security through which ransomware infections propagate. Ransomware is spread using social engineering tricks via social networking sites and email attachments. It is very similar to the infamous FBI Moneypak virus. Spammed email messages are the major contributor in ransomware propagation. The remaining entries are the top four ransomware family detection counts.
Another interesting gauge for us in determining the rise of ransomware activity that is souring the Internet is the popularity of Thirtyseven4’s free Cryptobit decryption tool. The Cryptobit decryption tool was made available to the public on the http://thirtyseven4.com website in late April of last year. Since that time the tool has been downloaded 232,337 times. Of those total downloads, 18.65% of them came in last month. The top five countries requesting downloads included: USA, Australia, India, Czech Republic and Italy.
While I mentioned at the top of the column I’m not the type of guy you’ll ever see harvesting blocks of ice out of Lake Erie this winter, I’ll admit that I’ve sang every track on the Frozen CD a billion times with my daughter (inside next to a fireplace!), and none more often than the hit song “Let it go”. Taken directly from the song: if you want “Don't let them in, don't let them see“ to be your motto for malware, especially ransomware, then I might suggest installing strong antivirus software like Thirtyseven4 Endpoint Security (which includes the noted Behavior Detection System, as well as Email Security and Browser Sandbox all very important for keeping ransomware off a system).
I’d also like to quickly suggest the following:
[1] Change passwords frequently
[2] Only open email attachments coming from a trusted source
[3] Don’t follow links within emails without knowing what they link to. In other words, “Turn my back and slam the door! “
[4] Apply the latest security updates whenever required/prompted by your installed applications - such as Windows and MAC OS updates, Java, Adobe updates, etc.
[5] Limit access to removable drives and shared drives. And in doing so, “…the fears that once controlled me can’t get to me at all!”
OK, Your turn to be honest: how many of you actually started singing the lyrics after just reading them?
More information on Ransomware has been posted here.
 |